-
Meet device management for Apple Watch
Organizations can now deploy and configure Apple Watch in addition to other Apple devices. Learn how to implement device management for watchOS to help organizations improve productivity, support wellness, and provide additional support for their employees.
Resources
Related Videos
WWDC23
-
Search this video…
♪ ♪ Melissa: Hi, I’m Melissa Nierle. I’m a software engineer on the Enterprise and Education Technologies team, and today I’m excited to introduce you to device management for Apple Watch.
Apple Watch has become an indispensable daily companion for users by helping us stay connected, active, and healthy.
Hands-free communication, responding to notifications on the go, and safety features like fall detection make Apple Watch the perfect addition for enterprise customers.
From small businesses and public utilities to large enterprises and healthcare systems, there’s no limit to the places where you’ll find Apple Watch at work. Companies like Volvo already use Apple Watch to enhance their employee workflow by using it to log jobs and streamline communication with customers. We want to enable organizations to create solutions that improve productivity, support wellness, and provide additional safety by deploying Apple Watch to their employees. That’s why this year, we’re introducing Device Management for watchOS.
Organizations can now deploy and configure Apple Watches along with all their other Apple devices.
We’re excited to see all the ways Apple Watch will impact both users and their organizations when deployed at scale.
Let’s get started with how it works. First, we’ll discuss the new enrollment flow for Apple Watch, and then later, we’ll talk about what you need to know when managing Apple Watch.
There are a few things we should consider when Apple Watch enrolls into MDM.
First, just like how we use Apple Watch and iPhone together as a pair, they are managed together as a pair as well.
The devices share functionality between them like apps and restrictions, as well as hand off information to each other to perform tasks in one seamless flow.
We’ve leveraged this to create the Apple Watch enrollment flow.
The enrollment flow actually begins on iPhone for both the organization administrator and the end user. The host iPhone will need to already be enrolled with MDM, and supervised in order to perform the watch enrollment flow.
MDM enrollment happens during the watch pairing flow, so you will need to begin with a new or reset Apple Watch.
Existing paired Apple Watches will need to be reset in order to be enrolled. The Apple Watch enrollment flow utilizes declarative device management so your server will need to support both Apple Watch and Declarative Device Management to enroll Apple Watch.
Check out what’s new this year in declarative device management by checking out its session. Now that we know the prerequisites, let's dive into the enrollment flow step by step.
We start with a managed and supervised iPhone.
First, the organization administrator will send a new declaration to the phone.
This is the new Watch Enrollment configuration. It signifies to the iPhone that any Apple Watch that pairs to it should be enrolled into MDM.
Here is the content of that configuration. Let's take a look at the payload keys.
First is the key for the enrollment URL endpoint.
This endpoint delivers the MDM profile that the Apple Watch will download and install.
The MDM profile for Apple Watch is just like the MDM profiles already used for iOS and macOS devices.
The next key, AnchorCertificateAssetReferences, is an optional item and specifies an array of anchor certificates.
These anchor certs will be used to evaluate the trust of the enrollment profile server.
Each anchor certificate used in this flow must be included in an asset declaration already present on the iPhone.
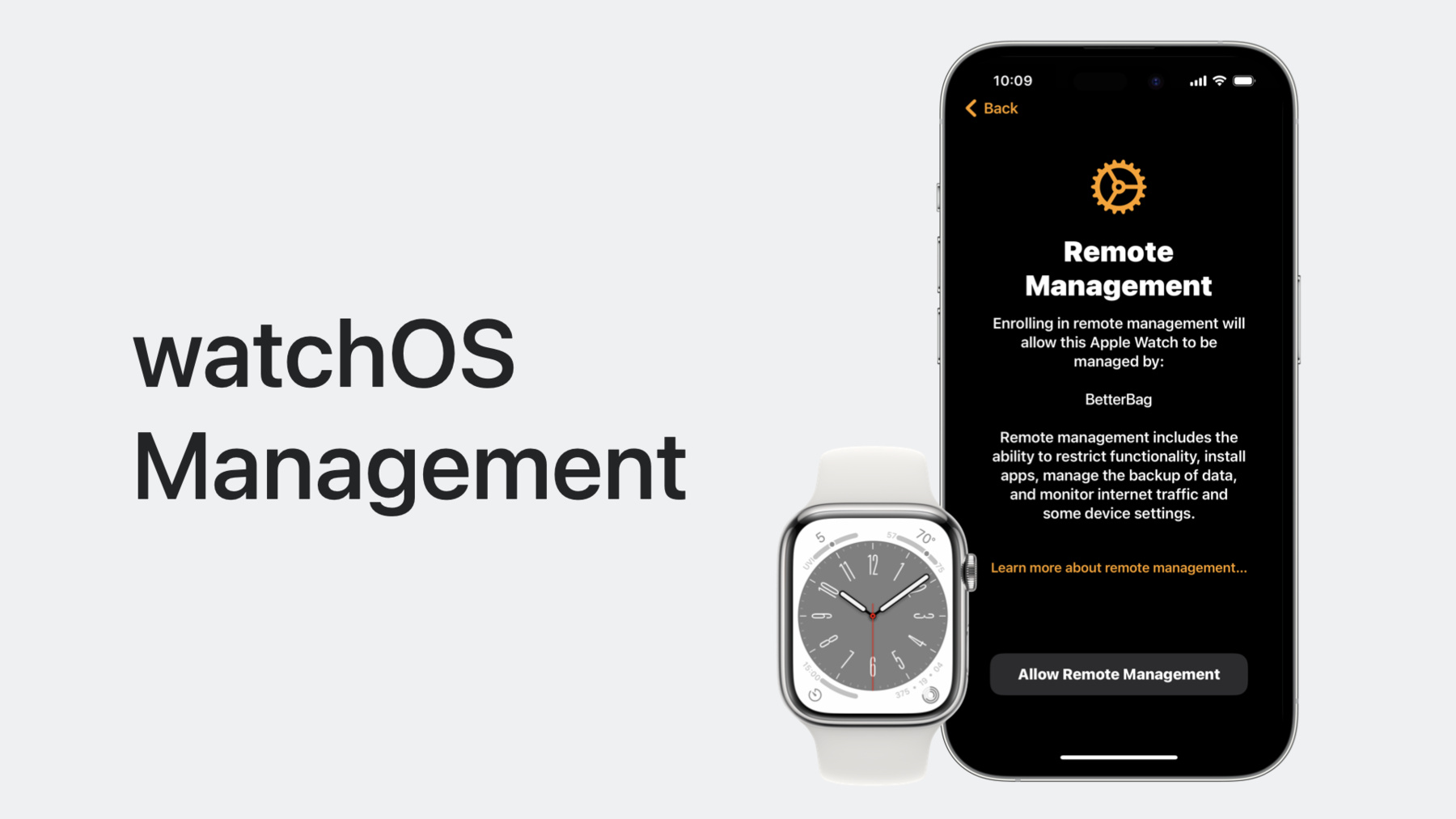
Now that the configuration is installed, let’s bring in Apple Watch. Like I mentioned, the Apple Watch will be in its pairing state, and once the user initiates pairing from the phone, they will be prompted to accept Remote Management.
Here. the user will need to allow remote management for their Watch to continue.
If they don’t accept remote management, the pairing flow will end without the Watch getting set up. The enrollment flow for Apple Watch is designed with security in mind to address the need to manage iPhone and Apple Watch together as a pair.
There are two key pieces to ensure security.
First, the administrator needs to verify that the host iPhone is enrolled into an MDM server managed by their organization.
Secondly, they need to be able to identity which iPhones and Apple Watches are paired together. Let’s see how we accomplish that with this new enrollment flow.
During Watch pairing, the iPhone sends information from its Watch enrollment configuration to the Apple Watch.
The Apple Watch uses the URL and any provided anchor certificates to make initial contact with the server.
Within this request, it will provide signed machine info. Upon receiving the enrollment request from the Apple Watch, the server will inspect the machine info data and look for a new "pairing token" key.
Because the pairing token key will not be present on this first attempt, the server will issue an HTTP 403 response.
Here’s what that 403 response will look like.
First, the error code tells us that the Watch pairing token is missing from the request.
Then, within the details dictionary, you will provide a security-token.
This random UUID string will be used by the Watch to kick off the pairing token retrieval flow. The Watch sends this security-token to the iPhone. The iPhone performs a GetToken checkIn request, which includes both the phone and Watch UDID, as well as the security token received from the Watch’s MDM server.
Here’s what this new checkin request looks like. We’ve added a new CheckIn message type this year called the “get token” check in request.
This new message type allows the device to request secure tokens for various services the MDM server supports.
The TokenServiceType key indicates which service we are requesting a token for.
Here, the value indicates it needs a Watch pairing token.
Next, the TokenParameters key is a dictionary containing parameters specific to the token service type. For the Watch pairing token, the phone includes the security token from the Watch, its own UDID, and the Apple Watch’s UDID. The MDM server takes this information and uses it to generate a secure pairing token that can be verified by the Apple Watch’s MDM server upon receipt. Here, the MDM server can create the correct relationship between the iPhone and Apple Watch based on the received UDIDs. The server finishes by sending its generated pairing token to the iPhone.
Here’s an example of what that token response from the server will look like. The token is in the form of base64 encoded data.
Upon receipt, the phone sends the pairing token to the Apple Watch.
The pairing token is then added into the Watch’s Machine Info, and sent back to the MDM server in a new enrollment request.
Here’s an example of the Apple Watch machine info sent to the server with the secure pairing token included.
The MDM server securely verifies the pairing token it received with the machine info, and can therefore confirm the identity of the iPhone’s MDM server and the paired relationship between the iPhone and Apple Watch.
Now the server returns the MDM enrollment profile to the Apple Watch.
The user will finish the steps on the phone to complete Apple Watch setup, and the Enrollment profile will be installed on the Apple Watch at the end of the pairing flow. Just like on iOS, enrollment is officially complete when the Apple Watch sends a CheckIn request with the Authenticate messageType.
And now Apple Watch is enrolled and supervised! With this specialized enrollment flow, you will want to keep a few things in mind for Apple Watch. First, when building your device management solution, utilize the data sent to the server during enrollment to detect which Apple Watch is paired to which iPhone.
Use this information to create an intuitive UI for IT administrators who will need to identify the pairs.
Keep in mind that once the Watch Enrollment configuration is applied to the phone, all Apple Watches that begin to pair with the phone will be prompted to enroll into management.
However, any Apple Watches already paired to the phone will not be affected and would need to be wiped and paired again in order to be enrolled.
And lastly, remember that Apple Watch is supervised once its enrolled, so you can add it to all of your workflows for organization owned devices.
And just like with iOS, health information and fitness activity is never sent to the MDM server. Now that we know how to enroll Apple Watch, let’s talk about how you’ll manage it.
We are starting right out of the gate with declarative device management support for watchOS.
In watchOS 10, all declaration types are supported on watchOS.
Predicates in activation declarations are supported as well, so you can build custom multi-step management workflows right on the Watch. The status channel has also made its way to Apple Watch, so you will be able to receive proactive updates from all of your Apple devices.
Here’s a look at the declarative device management features in watchOS 10.
Find the full list of support in our open source schema and developer documentation that has been updated to reflect availability on watchOS. Of course, the MDM protocol is also supported on managed watches. Payloads, restrictions, and MDM commands and queries can all be sent to the Apple Watch, just as you do today for your other Apple devices.
There’s a wide range of supported MDM features for watchOS this year. Let’s talk about a few of the available configuration payloads.
First we have our suite of networking capabilities. New this year in watchOS 10 is the ability to have a dedicated VPN installed on Apple Watch.
In addition to our existing networking payloads, Wi-Fi and Cellular, we’ve also brought support for the per-app VPN payload to watchOS.
Now you can equip all your Apple devices with access to your secure enterprise VPN.
Next, let's talk about the payloads you can use to ensure security on watchOS.
The same payloads you already use to install SCEP and ACME certificates, enforce passcode rules, and apply restrictions on your Apple devices are now all supported for watchOS.
The password policy and restrictions payloads both share unique behavior on watchOS. Let’s cover that now.
Restrictions and passcode rules that are applied to iPhone will be synced to the paired Apple Watch.
For example, if you apply a passcode enforcement policy to the iPhone, the paired managed Watch will prompt the user to create a passcode for it as well.
If an alphanumeric password is required by the iPhone’s policy, the user will need to use their iPhone in order to unlock their Apple Watch, Like, for instance, when it's taken off their wrist. However, both Restriction payloads and password payloads applied directly to Apple Watch will not be synced back to iPhone. Use this detail in the directionality of the rules to customize your restrictions and password policy payloads for each platform. MDM queries are helpful to learn the current status of the device and its content. These queries, of course, operate in a polling manner, from the server to the device.
Instead of constantly polling the Apple Watch with queries, you should instead use the status channel of declarative device management. This way, the Apple Watch proactively tells the server whenever a change occurs to a status item the server subscribes to.
Now, let's turn to commands that you'll want to consider for watchOS.
The same commands from iOS are supported on watchOS to ensure the integrity of the enterprise data on your Apple Watch.
You can remotely clear the passcode, lock and erase the device as needed.
Un-enrolling from MDM by removing the profile is also supported for watchOS, but it has different on-device behavior.
Let’s look at that now.
Removing the MDM profile from Apple Watch, whether by a user or via MDM command, causes it to be unenrolled from the server.
When Apple Watch is unenrolled, it is unpaired from its host iPhone and its content and settings are all erased.
Un-enrolling Apple Watch will not effect the enrollment status of its host iPhone.
Now, if the host iPhone becomes unenrolled, whether by the user or the organization, it will trigger the Watch to be unenrolled as well.
Therefore, removing management from the host iPhone will ultimately result in the managed Apple Watch being unpaired and reset. The last piece of the MDM protocol we will want to discuss is app deployment.
On watchOS, there are three different kinds of apps.
First, there are Paired apps, which are watch apps that share data between itself and its complementary iPhone app, but the Watch app can function on its own in the absence of the iPhone app.
Next, there are dependent watchOS apps.
These Apple Watch apps require a companion iPhone app to be functional.
And lastly, there are Standalone watchOS apps. These apps exist only on the watchOS platform and have no iOS companion app.
For both the Paired and Dependent watchOS app types, administrators will need to manage these apps together across the two devices.
Standalone watchOS apps are also supported.
These apps will only need the App Install command sent to the Apple Watch. When installing paired and dependent apps to iPhone and Apple Watch, the app should be installed to the iPhone first.
Then, once you ensure the app installed on iPhone, send the install app command to Apple Watch. When updating Paired or Dependent watchOS app types, both the phone and the Watch app will need to be sent commands to update their apps.
Similarly, when deleting paired or dependent apps, the remove command will need to be sent to both Apple Watch and iPhone in order to ensure correct behavior.
Managing paired and dependent iPhone and Apple Watch apps in tandem like this will make for the best user experience and the smoothest workflow for administrators because it ensures apps are available and properly managed.
That’s just a small glimpse of all the things you can do with managing Apple Watch.
Understanding these best practices we’ve gone over is the best way to ensure a smooth adoption and ramp up of your watchOS management.
Let's summarize some of the key points now. Administrators will need to manage iPhones and watchOS together as a pair, so make sure your MDM products are built with this relationship in mind.
Creating combined workflows and exposing the device relationships in your UI will help admins keep the two platforms in sync with each other.
Take advantage of the proactive status channel built into Declarative Device Management to avoid constantly polling the device for information, which could be a drain on power.
The Declarative Device Management status channel will update the server whenever a meaningful change occurs.
Although there are new considerations for managing Apple Watch, the MDM protocol together with the Declarative Device Management features are all the same tools you’re familiar with using already, so you’ll be able to get started with managing Apple Watch today.
Let's wrap up what we’ve discussed today about Apple Watch.
Apple Watch is now manageable in watchOS 10, paired to a supervised iPhone running iOS 17.
Begin implementing your Apple Watch enrollment and management support for your MDM solutions today to empower IT admins and their organizations to make their enterprise Apple Watch workflows as easy as possible. Admins, start planning how managed Apple Watch will optimize your organization’s productivity and end user’s connectivity and well-being.
We’re excited to learn about the Apple Watch workflows you plan to implement and how it will improve your organization's digital ecosystem.
And whether you are the MDM developer or admin looking to deploy Apple Watch, we want to hear from you.
Be sure to file feedback requests at feedback.apple.com.
And finally, check out our other sessions this week on declarative device management as well as everything else that’s new in managing Apple Devices. That’s Device Management for Apple Watch.
Thanks for being here today, and have a great week!
-