-
Deploy iOS 15 in your organization
Discover the latest platform changes for deploying iOS 15 and iPadOS 15 in your business or education organization. Learn about deploying both organization-owned and personally-owned iPhone and iPad devices. Explore fundamentals and new updates for deployment workflows including enrollment, ongoing management, content distribution, and re-deployment.
Resources
- AppleCare Professional Support
- Apple Platform Security
- Apple School Manager User Guide
- Apple Business Manager User Guide
- Apple Platform Deployment
Related Videos
Tech Talks
WWDC21
- Discover account-driven User Enrollment
- Manage software updates in your organization
- What’s new in managing Apple devices
WWDC20
-
Search this video…
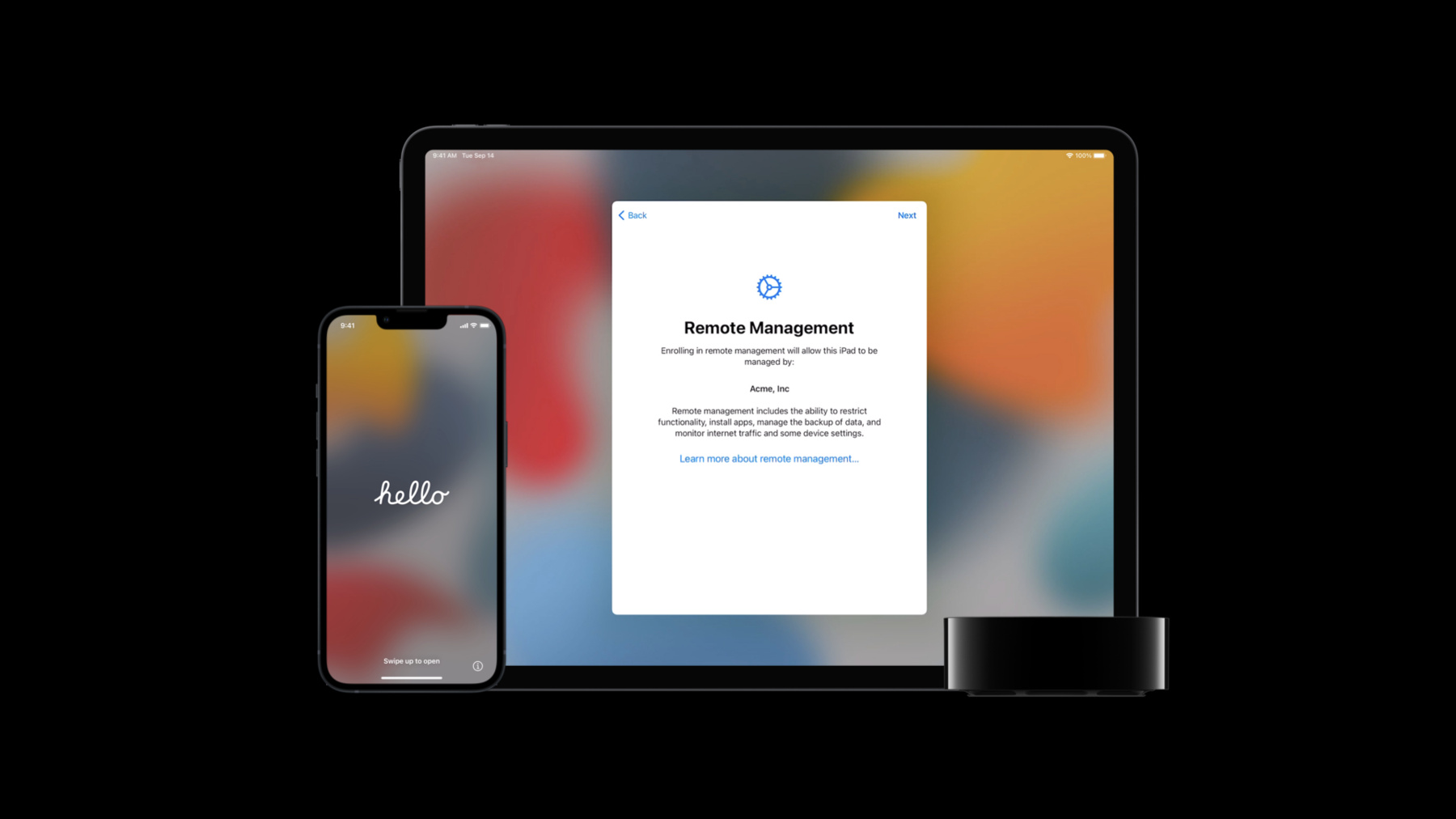
Alexandre Morin: Hello, my name is Alexandre Morin, and I'm a senior consulting engineer supporting enterprise and education customers worldwide and sometimes just beyond. I specialize in device and content management and I'm excited to tell you about deploying iOS 15 and iPadOS 15 in your environment. iOS 15 brings new ways to stay connected, powerful tools to help you focus on tasks, exciting updates for Maps, and new privacy features improve transparency and give you more control over your data. With iPadOS 15, it's easier to get things done and find and organize information, and multitasking is also easier to use and discover. You can now place widgets among the apps on your Home screen and jot down a comment or idea on any app or screen with Quick Note. iOS 15 and iPadOS 15 also bring updates specifically for device management, which improve the way you deploy and manage devices in an education or enterprise environment. At WWDC 2021, a number of sessions brought you details on these updates and new capabilities. "What's new in managing Apple devices" is a great starting point for these sessions. My colleagues Graham and Nadia introduce you to the refreshed device management experience in Settings and essential new management controls like Managed Pasteboard. In this session, we'll go through fundamentals of deploying iOS and iPadOS devices at scale and a few new device management updates since WWDC 2021. The technology underlying all the management capabilities we will discuss today is Mobile Device Management, or MDM. It is a framework we made available to developers to create device management solutions. These solutions may differ in user interface and market focus, but they all work from the same set of Apple-defined APIs. The first key decisions when bringing iOS and iPadOS devices into your organization are the device ownership model and the connectivity options. Who owns the device has a big impact on the device management capabilities available to you. If you choose to purchase devices and provide them to your employees or students, you'll have the most complete set of management capabilities for those devices. You might choose to provide one to each user -- referred to as a one-to-one deployment -- or devices can be rotated among users, which is referred to as a shared deployment. If you're instead supporting user-owned devices, you'll have a more limited set of management capabilities that provide more control to the owner of the device. The second initial decision is the type of connectivity to provide to those devices. Whether the devices are organization-owned or user-owned, you may choose to provide cellular service for those devices in addition to Wi-Fi. You may even be interested in a private cellular network or an emergency services option. On iPad, providing cellular connectivity can transform the usage patterns of your employees or students, such as with the new iPad mini which supports 5G. When deploying cellular-enabled devices, you'll need to consider the type of SIM that will be used: a physical SIM or an eSIM. Unlike physical SIMs, which are easily removed and are prone to theft or loss, eSIMs are software based and can be locked on the device with an MDM restriction. They are also much easier to deploy at scale since they can be installed on hundreds, thousands, or tens of thousands of devices using MDM. This is much more efficient and cost-effective than physically inserting SIMs. Another advantage of eSIM technology is that you can use MDM to try out or change carriers in your environment without having to get new SIM cards and physical access to each device. Because of these benefits, eSIMs are ideal for deploying large numbers of cellular-enabled devices. Recent iPhone models support Dual SIM, which allows you to have two voice lines active at once. This could be a business and a personal line, or two business lines with different carriers for employees out in the field, like first responders or field workers. Typically, this is enabled with a physical SIM and an eSIM. iPhone 13 has support for dual eSIM, giving you even more flexibility in your cellular deployment. You can provision one or both for your users with MDM or let users manage one of those two eSIMs as their needs change. Once you've selected an ownership model and device connectivity options, you need to deploy and manage these devices. Since all aspects of your deployment will be driven by whether you or the user owns the device, we will cover those two scenarios separately. First let's review deploying devices that your organization has purchased and will provide to the employee or student. We will cover these four areas, which come together to form a great deployment strategy: enrollment, ongoing management, content, and redeployment. Let's start with enrollment for your organization-owned devices. The best enrollment experience for organization-owned devices is Automated Device Enrollment. It allows for zero-touch deployment workflows for your devices. Devices going through Automated Device Enrollment are automatically supervised, which gives you access to the entirety of the management options defined by Apple. This method allows you to customize enrollment based on your needs. You can display custom branding or consent text. You can also secure the device setup process using modern authentication services such as Azure AD, Okta, Ping, and others. Finally you can choose to skip some setup assistant screens including the screens shown after a software update -- which, I should note, will also skip those screens for any future software updates, a great feature for unattended devices like kiosks. Note that this is the only enrollment method that prevents users from removing management. This process is all enabled with a web-based portal called Apple School Manager or Apple Business Manager. The devices you purchase from Apple or authorized resellers appear there and can be automatically assigned to your MDM server. When your devices are unboxed and activated, this portal will instruct them to enroll to your MDM and apply the enrollment settings you define in MDM. If you have devices that you acquired outside of Apple or authorized resellers, you can manually add iPhone, iPad, and Apple TV devices to Apple School Manager or Apple Business Manager with Apple Configurator 2 on Mac. When manually adding devices, there is a 30-day provisional period during which the user may opt out and remove the device from management. After the 30 days expire, the device is permanently added. Once the devices are in Apple School Manager or Apple Business Manager, they'll follow enrollment settings that you've defined in your MDM. A one-to-one device will typically be set up by the end user right out of the box. This is where the ability to skip specific setup assistant screens makes the setup smoother for the user. After selecting language and country, enrollment to MDM is integrated right into the familiar setup assistant experience. For a device that will rotate between users, you may use enrollment settings to enable Shared iPad. This feature enables you to provide a personalized experience to each student or employee who uses the shared device, much like they would have on a one-to-one device. For all deployment types, Apple Configurator 2 helps to make initial device-provisioning operations smoother and faster. You can provision dozens of devices at a time without ever having to touch the glass. If you do not have access to Apple School Manager or Apple Business Manager in your area, there is an alternative to Automated Device Enrollment which is called Device Enrollment. It can allow you to still be able to deploy the devices you own in a strongly managed way. To achieve this, you use Apple Configurator 2 to enable supervision on your devices over USB and use Device Enrollment to enroll them to MDM. Both can be done as a single operation with Apple Configurator 2. You will not benefit from the lock MDM feature that comes with Apple School Manager or Apple Business Manager enrollments, but you will still benefit from most of the features we're reviewing. Now that devices you own are enrolled, let's talk about ongoing management. As we discussed earlier, MDM management is built right into the operating system of every iOS and iPadOS device. The Settings app makes it clear to both your users and yourself as to the management state of the device and what MDM capabilities are in use. Those capabilities can be classified as payloads, restrictions, tasks, or queries. Configuration profiles consist of payloads that load settings and authorization information onto Apple devices. This automates the configuration of settings, accounts, restrictions, and credentials. With these different payload types, you can enforce passcode policies, restrict access to the Camera in sensitive environments, or deploy custom fonts. Mail, Contacts, and Calendar account information can be configured for users. Network information like Wi-Fi and VPN can be set up for your devices, as well as the certificates required for those connections. Some of the most important MDM payloads for your deployments are restrictions. They allow you to enforce your security policies and help users stay focused on their task. Commonly used restrictions allow you to lock device names, disable iCloud services or the App Store, which prevents users from installing third-party apps. But even then, you are still able to deploy apps with MDM. You can even hide or show any apps you want on the Home screen, be they third-party apps or most system apps. At WWDC we announced a new restriction called Managed Pasteboard that supplements Managed Open In. Managed Open In prevents attachments or documents from managed sources from being accidentally opened in unmanaged destinations and vice versa. For example, a confidential email attachment is not allowed to be opened in a user's personal apps. And mirroring that behavior, you may also prevent their personal document from accidentally entering the organizational data stream. We announced iCloud Private Relay at WWDC as a way to enhance user privacy and help users' traffic stay private. And new since WWDC, we introduced a supervised restriction to allow you to disable iCloud Private Relay on your devices. At the time, we also let network administrators know that they could restrict this feature by returning a negative DNS response for mask.icloud.com. Since then, we added a second host: mask-h2.icloud.com. Let's detail a few more helpful restriction examples. Managing USB pairing is important for securing access to a device over a physical connection but also to allow access for IT tasks like gathering logs. Historically, IT admins have used an enrollment setting to prevent any connections of USB. This method is deprecated and there is a more modern and flexible method available to you: the supervised allowHostPairing restriction. With this restriction in place, only computers that possess the same supervision identity as your iOS and iPadOS devices will be allowed access over USB. The main advantage to this method is that you do not need to restore devices to change these settings. If you need access, you're not locked out. Finally, you've likely already had users ask for help in clearing their device passcode after they forgot it. If the user has restarted their Wi-Fi-only device since the last time they successfully unlocked it, the Wi-Fi credentials remain encrypted, the device is off-network, and MDM cannot reach it to send a clear passcode command. An Ethernet adapter can be quite useful in this scenario. If you have previously disabled USBRestrictedMode, the Ethernet connection will be active at this stage and the clear passcode command will reach the device successfully. This is one example of weighing the security benefits of a restriction versus the related support considerations. Sometimes full lockdown can be detrimental. A device enrolled in MDM can also be administered through a number of direct management tasks, giving you powerful remote capabilities. Management task can take specific actions on devices like installing apps, remotely wiping a device, or installing a software update. Tasks to highlight here are Lost Mode and Activation Lock. For locating lost or misplaced devices, you have Managed Lost Mode. You use MDM to place a device directly in Lost Mode. During this time, MDM can collect location information for the device or make it emit an audible alert. The device is locked with a customized message with contact information for your organization, so anyone finding the device is aware that it is being tracked. And after MDM takes the device out of Lost Mode, the Lock Screen displays a message informing the user that this device has been geolocated and when. Most importantly, Lost Mode does not require the user to use iCloud or to grant access to Location Services. Actually, Location Services can be turned off and Lost Mode will still work. The privacy notifications of Lost Mode strike a balance between user privacy and IT control. Theft deterrence is made easy for Apple School Manager or Apple Business Manager devices with device-based Activation Lock. By leveraging device-based Activation Lock, MDM enables or disables Activation Lock directly with Apple's servers without the need to interact with the device or a user's iCloud account. For devices you own, you should use this exclusively and not allow users to Activation Lock your devices with their iCloud account. If you do let users leverage user-based Activation Lock, MDM can still gather a bypass code and use it to clear Activation Lock with a command sent to the device. MDM can query your managed devices so you can check their status and ensure they meet your compliance standards. The inventory updates sent to your MDM enable you to get the name of your devices, which can also be remotely set and locked. Battery level data can help you get a sense of your user's ability to get all-day battery life, and roaming status can help alert you to potentially costly cellular charges. And of course, compliance through passcode requirements helps ensure that your devices and data are secured with data protection. Many of your device management goals are achieved when your MDM solution combines a set of restrictions, queries, and tasks, such as in the critical case of managing and deploying software updates. In "Manage software updates in your organization" my colleague Lucy covered software update management. Let's review and add a few additional details as you prepare to deploy iOS 15. When a beta software update is released, you use AppleSeed for IT to obtain it and test it in your environment. AppleSeed for IT is a great way to access IT-specific release notes and test plans and file direct feedback. Learn more about AppleSeed for IT in a WWDC 2020 session. If you require more time to validate the software update in your environment than the beta cycle, you can defer updates for up to 90 days. On iOS and iPadOS, all updates have the same deferral value applied to them. Deferral means that updates that would otherwise be shown to the user in Settings are instead hidden until the deferral window expires. Deferral does not affect the ability to update a device using MDM commands, Apple Configurator 2, or the macOS Finder. You can use MDM to install the latest OS or a specific OS version on your supervised devices, even while the deferred update is hidden from the user. And new since WWDC 2021, you can now defer beta updates to test your deferral workflow during the beta cycle instead of needing to wait for a public release. When you're ready to update devices and you send an MDM install command, the device prompts the user with the update and describes it as required by your organization. All updates sent by MDM are treated as required updates and can only be delayed by the user up to three times. After the third time the user delays, the device will require the user to update in order to continue to use the device with the exception of emergency calling. Any update on a device with a passcode requires the user to enter it for authorization. Starting with iOS and iPadOS 15, users running iOS and iPadOS 14.5 and later may now see the option to choose between two software update versions. This allows users to update to the latest version of iOS and iPadOS 15 as soon as it is released. Or they can continue on iOS and iPadOS 14 and still get important security updates. The choices will be available for a period of time. MDM can control which options are offered with the new RecommendationCadence key in the Settings command. And of course, these update options will respect the software update deferral window you have set. With a RecommendationCadence of 0, the user is presented with the option to update to iOS 14 or iOS 15 releases. With a RecommendationCadence of 1, the user is only presented the option to update to iOS 14 releases. And with a RecommendationCadence of 2, the user is only presented the option to update to iOS 15 releases. In each case, any deferral policy you set is respected. While your MDM solution works to add support for these update options, you may also be able to send a custom command provided here to set the RecommendationCadence on your devices. I mentioned Shared iPad before and wanted to give you a little more detail on what to consider when enabling Shared iPad. Users sign in with the Managed Apple ID that you create in Apple School Manager or Apple Business Manager, If you're an education organization, you can sync with your student information system to automatically create the Managed Apple IDs, or if you use Azure Active Directory, you can federate to leverage existing credentials. For users without credentials, temporary session provides them a way to log into Shared iPad and leave no data behind. Shared iPad works with content caching, which we'll describe soon when we review getting content on the device. You can also use tethered caching where a Mac is providing content caching and Ethernet connectivity over USB to a cart of Shared iPad devices, offloading your Wi-Fi network from app and iPad OS update traffic. Now that your devices are enrolled and managed, let's look at deploying content. You'll provide apps and books to your employees or students using Apple School Manager or Apple Business Manager, where you obtain content licenses. You can purchase licenses for third-party App Store apps, books from Apple Books, and custom apps. Custom apps are made specifically for you by internal or external developers, only you can purchase them in Apple School Manager or Apple Business Manager, and these apps are hosted by Apple but they're not available to the general public. Apple provides both device-based and user-based app distribution. For organization-owned devices, you should use device-based app distribution. Once you acquire the licenses, you use MDM to assign and distribute apps directly to a device. This does not require you to configure an Apple ID on each device or send an invitation to each user. You maintain full ownership of the app licenses and can revoke them from the device and reassign them to different devices.
To provide your users with a great experience and reduce network slowdowns, enable content caching on your network. This service is built into macOS and allows you to cache commonly downloaded assets locally. You can cache assets such as App Store apps, books, or iCloud content, which is helpful when Shared iPad is syncing user content. And perhaps the most helpful is the ability to cache software updates for when MDM or users update devices on your network.
To have a successful and scalable one-to-one deployment, limit the number of apps deployed initially to one or a few. This way, you provide initial access and productivity quickly for your users while giving them control of installing additional apps on their device as the need arises. This also moves the majority of your app deployment traffic out of band, distributing that traffic over time and different networks. For Shared iPad deployments, user-driven app installs are not recommended. You want to install all apps to all Shared iPad devices and then use the MDM show/hide apps payload to tailor the app selection for the needs of each user, based on group membership. This avoids delays caused by the need to install apps each time users log in. Now that you know how to manage content for your devices, let's review how to redeploy or repurpose devices.
When redeploying or repurposing devices, you want to ensure that your organization's data and user data are securely erased. With the device in hand, you or the user can use the Erase All Content and Settings option in Settings to obliterate all of the encryption keys, rendering all user data on the device cryptographically inaccessible. It's an ideal way to be sure all personal information is removed from a device before giving it to somebody else, returning it for service, or turning it in for an upgrade. This can also be done using Apple Configurator 2, the macOS Finder, or the remote wipe MDM command. So far, we've reviewed four key areas of deployment for devices that your organization purchases and provides to employees or students. You may instead need to manage user-owned devices or have a mix of both. Let's examine these same four deployment phases for user-owned devices. As before, it starts with enrollment. For user-owned devices, there's User Enrollment. User Enrollment is designed specifically for when employees or students bring their own devices to use inside your organization. You use User Enrollment to protect the privacy of personal data while still securing your organization's data on the device. My colleagues Timm and Melissa introduced major improvements to the onboarding and authentication capabilities of User Enrollment in the "Discover account-driven User Enrollment" session at WWDC21. Let's go over the basics of User Enrollment and add some more details to that session's great content. User Enrollment requires Managed Apple IDs. These IDs are owned and managed by the organization and provide access to Apple services such as iCloud. You can use federation or SIS sync to provide these to your users. In User Enrollment, Managed Apple IDs are used in addition to a personal Apple ID. Managed and unmanaged apps use the correct iCloud account automatically. Data separation ensures your data and the user's are isolated from each other in distinct, cryptographically separated APFS volumes. In iOS and iPadOS 15, there are new updates to User Enrollment that make it better than ever to support personal devices. Much like in Automated Device Enrollment, where we leverage the familiar setup assistant experience, iOS 15 and iPadOS 15 use a similar approach to streamline the User Enrollment process. Users are used to setting up accounts and settings, so initiating User Enrollment will be intuitive for them.
If you are unable to provide Managed Apple IDs to your users, or do not have access to Apple School Manager or Apple Business Manager, another option for enrolling user-owned devices is Device Enrollment. This enrollment type offers less user privacy than User Enrollment, so users may be more careful in their decision to enroll to your MDM on their personal devices. When given the option between the two, choose User Enrollment. Once your users have chosen to enroll their personal devices to your MDM, you then have a specific set of management capabilities available to you. User Enrollment management capabilities are curated specifically for BYOD, so you can configure your corporate accounts and VPN settings, and you may require passcodes on the user's device, but the policy may not require very long and overly complex passcodes. You can deploy managed apps but cannot take over a user's own apps. With these capabilities, you can get details about MDM-installed apps but not about personal apps. You cannot access personal information, a user's location, or remotely wipe the user's entire device. But you do have the ability to remove your organization's apps, accounts, and data at any time. This is how User Enrollment balances user privacy with the need to secure your data. User Enrollment fully supports Managed Open In so you benefit from the same strong data flow management capabilities offered on organizational devices, including the new Managed Pasteboard to help users avoid mistakenly moving data across the Managed Open In boundaries.
User Enrollment allows the user to log in with their personal Apple ID alongside their Managed Apple ID. So encourage users to enable Find My for them to personally manage a lost or misplaced device. And the same goes for Activation Lock. They own the device and they control the keys to locking their device. Those were the management capabilities that you get with User Enrollment. Let's discuss content deployment for these devices. As with the devices you own, you can purchase licenses in the apps and books section of Apple School Manager or Apple Business Manager. For organization-owned devices, you have device-based app distribution; for User Enrollment devices, you assign licenses to the user's Managed Apple ID. The user will need to approve the installation on their device, but as the Managed Apple ID and licenses are from the same Apple School Manager or Apple Business Manager, there are no additional Terms and Conditions prompts. You still retain full ownership of the app licenses and can reuse them at will. To help with getting a key app installed on your user-owned devices, at WWDC21, we announced Required App. If you have one app that you want to ensure is installed -- like an app catalog or a VPN app -- Required App allows you to specify that you would like it to be installed silently on these unsupervised devices, and this also works with custom apps. And to keep key managed apps installed on user-enrolled devices, you can mark them as nonremovable. The user will be alerted when attempting to remove these apps. Consider this for self-service, MDM-agent apps, or other critical apps and to complete the deployment for user-owned devices, or scenarios such as when users are upgrading their device or leaving the organization. Whatever the reason, there will come a time where user-owned devices will need to be removed from management. The user can process this unenrollment themselves on their device in Settings. You can also process this unenrollment using MDM. Additionally, a device being repurposed might be erased with Erase All Content and Settings, Apple Configurator 2, or Finder, which will effectively unenroll the device. If the employee or student is instead moving to a new device, only their personal data will be migrated. Once their new device is set up, they will proceed to do a fresh MDM enrollment on it, and they are back up and running. We've now covered the four key areas for both organization-owed and user-owned devices. Now let's review some resources that may be helpful in your iOS and iPadOS 15 deployment. As a reminder, AppleSeed for IT, which we covered earlier, allows you to access and download prerelease Apple software for testing in your environment, includes detailed test plans, and puts your feedback submissions into a dedicated queue for enterprise and education. Apple School Manager and Apple Business Manager guides are available to help you manage users' devices and content. The Apple Device Deployment Reference is a technical document on the topics we covered today and supporting information about MDM, infrastructure, and services integration. The Apple Platform Security documentation provides security information about all software, hardware, and services across the Apple platforms. And the AppleCare Professional Support website hosts program information for each of the AppleCare OS support offerings for IT departments and IT help desks, including AppleCare for Enterprise. We're excited to see you successfully deploy iOS and iPadOS in your environment. Thank you for watching.
-